Tor: An Amazing Browser That Flies Under the Radar
Here’s a beginner’s guide to what’s being called the Internet “anonymizer.”
If you surveyed most of your friends and associates and asked them what is personally important to them while using the Internet, they might use one of the following words:
- Speed
- Security
- Access
- Privacy
- Anonymity
What do you think they would say is the most important? How would they rank them? The fact of is, most of us don’t simply think about these things—we just hop on the Internet and do our thing. Does a web beacon exists?
To that point, if you asked yourself the same question, how would prioritize the list? What’s the highest on your list?
There’s no such thing as the average person on the Internet; we’re all likely to have different priorities for different reasons.
- As Internet users, we are as different as our personalities, work and personal responsibilities.
- We also use the Internet differently from each other based on our interests, obsessions, political affiliations, and hobbies.
When privacy comes out on top.
However, there are many people who use the Internet who definitely do not want to be identified by name on the Internet, at least when they’re doing certain activities if not all the time. They would like to stay anonymous, as often as they can, online.
- This isn’t simply a matter of not identifying themselves: they don’t want anyone to be able to track them down and find out who they are.
- They also want to visit any type of website they want without anybody knowing about it and stopping them…no matter the content, whether it borders on being illegal or is even outright illegal.
- They also want to say what they want, even if it’s not popular or raises concerns…and they don’t want to be put under surveillance, monitored, arrested, or worse. (After all, freedom of expression changes depending on what country you’re in.)
- Finally, they believe—with conviction, that we could be tracked down and identified very easily with the way the Internet and Web work today.
That’s where the very special Internet network known as Tor comes in for this crowd.
What is Tor?
Tor is a service that redirects Internet traffic through a special network that helps someone stay unidentifiable and unidentified online. Tor exists to keep an Internet user’s name and identity out of Internet activity (some or all) that they don’t want their true name and actual identity attached to.
Because, sometimes people simply want to communicate online, post messages, and view websites in private, but are afraid to.
That’s what Tor does.
What does Tor stand for?
Tor stands for The Onion Router, and it’s never spelled TOR or T.O.R., just so you know. It’s simply Tor.
Tor was developed in the mid-1990s by some computer scientists and a mathematician while working for the United States Naval Research Laboratory. They were tasked with coming up with a way to protect their Navy’s online intelligence communications.
Obviously, their goal wasn’t simply staying anonymous. They wanted to prevent others (an individual, organization, or foreign country) from stealing and deciphering the Navy’s communications.
Tor made available to the public.
In the ensuing years, Tor transformed from a special network for sending secure military communications to a network that was open to the world at large. An Internet inside the Internet, so to speak.
This happened with the creation of The Tor Project, which was developed between 2002-2005, and founded by some of the original creators. However, by then there were several organizations that recognized that Tor offered something special—the ability for anyone in the world to use the Internet and send messages and email anonymously.
Tor became a beacon for privacy and free speech advocates.
Where does the “onion” idea come in?
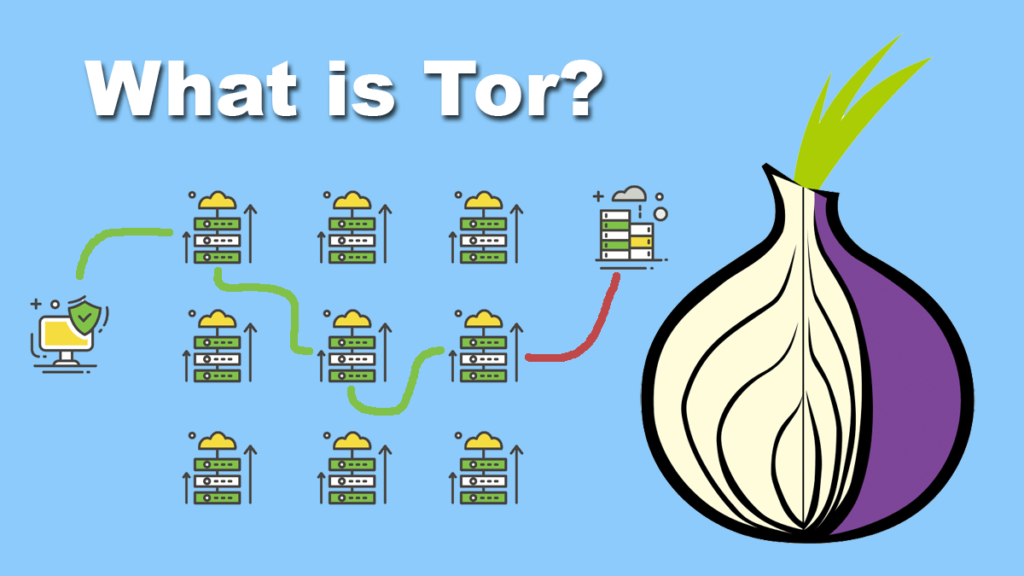
If you’ve ever peeled apart an onion, you know it comes apart in layers. The computer engineers who created Tor chose a method that added layers of encryption over data that was going across a network.
Along with that, they ingeniously created special stops along with the network, called relays, where a layer of encryption is pulled off, but just enough to get information the next relay destination. When the encrypted message arrives at the subsequent relay, the same thing happens—another layer is stripped and the message is moved on.
By the time the data reaches its destination, the last layer is peeled away and the information can be read. But everywhere along the way, nobody could see the data that was being transmitted. Not the contents and definitely not the IP address of the sender, which (if the person worked from one primarily locations) would identify where they were.
That also means if there were an intruder or hacker along with the network, they wouldn’t be able to know who the sender was.
Tor today.
Today, Tor is vibrant and growing in popularity and controversy. Tor is free, just like the Internet, and it moves Internet traffic from millions of users across a network of volunteer relays, numbering in the thousands.
However, as you start to look into Tor, be prepared. Because as you might expect, that level of freedom, which can be used for all the right reasons, is also abused by many people on the Internet…significantly…and for all the wrong reasons.
It all depends on what your perspective is on freedom of expression.
Download the Tor Browser today.
Related Articles
- Hide my IP
- What is a proxy server?
- Proxy server risks
- Official Website for Tor
Related Articles
- All
- Easy Prey Podcast
- General Topics
- Home Computing
- IP Addresses
- Networking Basics: Learn How Networks Work
- Online Privacy
- Online Safety
- Uncategorized
Ransomware Attacks: Strategies for Protection and Defense
The world of cyber threats is constantly evolving. Businesses face new and stronger threats every day. Ransomware…
[Read More]Privacy and Surveillance Issues Affect Your Personal Security
Many people these days are worried about their privacy. And from internet ads that feel like they’re…
[Read More]By Using Fake Email Addresses Scammers Are Trying to Fool You
A scammer can spoof an email address, a phone number, or a website by mixing or using...
[Read More]What is a Passkey? It’s a Smart Solution to Password Problems.
The main idea is this: A passkey can replace your password if you want it to. A...
[Read More]How to Identify Fake Crypto Exchanges and Protect Your Digital Assets
Fake crypto exchanges are one of the most common scams in the industry, using deceptive tactics to…
[Read More]Best VPNs at VPNTruRank: An Unbiased and Clear Look.
We may receive commission for purchases made through links in this post. Please read our affiliate disclosure.Now,…
[Read More]






